
Welcome back to another exciting installment of Exigo Insights!
Recently, I was working in a secure environment that called for Secured Remote Access to the Azure Vnet from internet without the need for assigning public IPs to the Azure VMs and have Multi factor Authentication on top of AD Authentication only for authorized users and desktops. So with that in mind, we’re going to talk about it right now.
Let’s talk about the details of integrating your Remote Desktop Gateway infrastructure with Azure Multi-Factor Authentication (MFA) using the Network Policy Server (NPS) extension for Microsoft Azure. This of course assumes that you have an RDS Deployment in your environment. If you do not, then this article is not for you. If you are planning on it, then this article may be something you want to consider.
The Network Policy Server (NPS) extension for Azure allows customers to safeguard Remote Authentication using Azure’s cloud-based Multi-Factor Authentication (MFA). Organizations can integrate NPS with Azure MFA to enhance security and provide a high level of compliance. This helps ensure that users establish two-step verification to log on to the Remote Desktop Gateway. For users to be granted access, they must provide their username/password combination along with information that the user has in their control. This information must be trusted and not easily duplicated, such as a cell phone number, landline number, application on a mobile device, and so on.
Previously, this kind of setup would have called for the configuration of the on-premises version of Azure MFA, which is where you would would have sent your RADIUS client requests from the Remote Desktop Gateway to in order to perform the MFA functions. Details on how this used to work can be found here. I’m still partial to this setup as it can server more than just securing RDP, but can handle ADFS, IIS, and other services as well. However, with the availability of the NPS extension for Azure, this now gives organizations the choice to deploy either an on-premises based MFA solution or a cloud-based MFA solution to secure RADIUS client authentication.
Visual Overview of Architecture
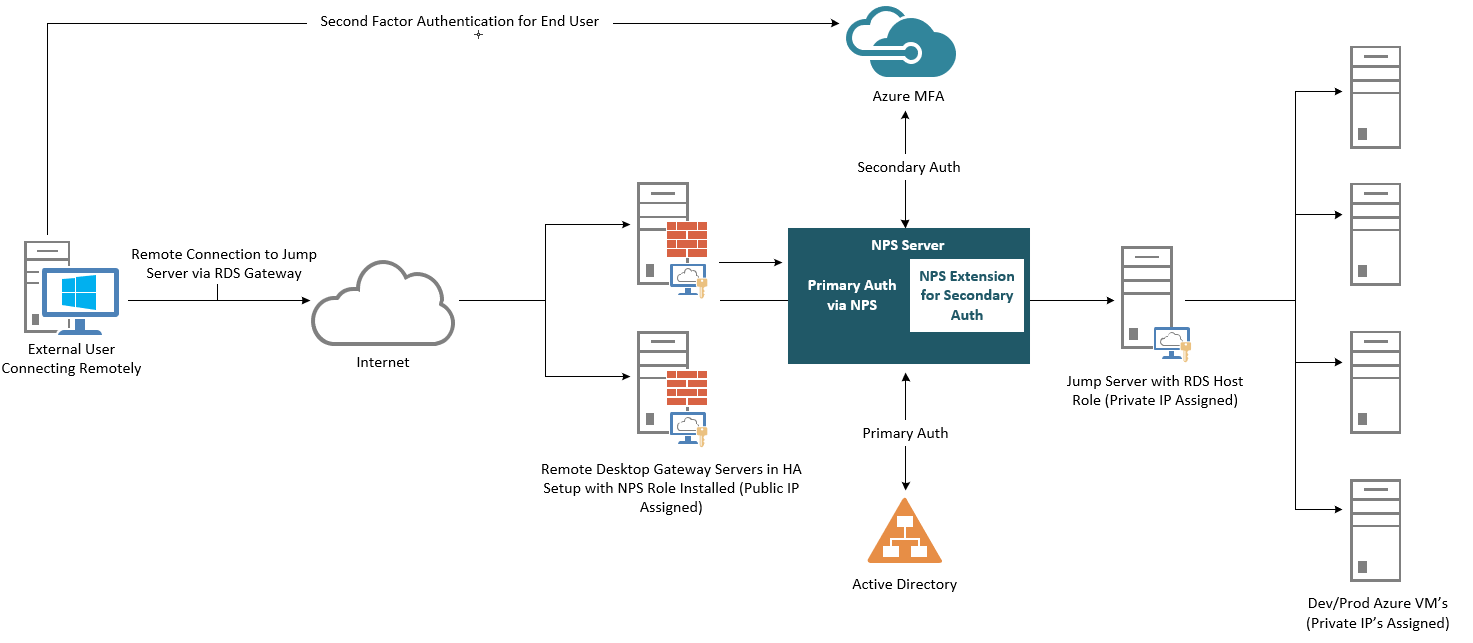
Authentication Flow
For users to be granted access to network resources through a Remote Desktop (RD) Gateway, they must meet the conditions specified in one Remote Desktop Connection Authorization Policy (RD CAP) and one Remote Desktop Resource Authorization Policy (RD RAP). RD CAPs specify who is authorized to connect to RD Gateways. RD RAPs specify the network resources, such as remote desktops or remote apps, that the user is allowed to connect to through the RD Gateway.
An RD Gateway can be configured to use a central policy store for RD CAPs. RD RAPs cannot use a central policy, as they are processed on the RD Gateway. When the NPS extension for Azure is integrated with the NPS and Remote Desktop Gateway, the successful authentication flow is as follows:
Prerequisites
This section details the prerequisites necessary before integrating Azure MFA with the Remote Desktop Gateway. Before you begin, you must have the following prerequisites in place:
Well, that wraps it up for this session of Exigo Insights. Stayed tuned as we will continue to explore the various Microsoft Solutions that can be done on-premises, in hybrid cloud, and fully public cloud.