
Hello there Exigo Insight faithful and welcome back! We’re glad you’re here. Today, we are going to cover a topic that is becoming all too common into today’s cyber world – Phishing scams. In the past couple of years, these scams have become far more rampant across the globe, and many companies, large and small, have fallen victim. So today, we will discuss Azure’s Multi-factor Authentication (MFA) solution, and how it can help protect your organization from falling victim to this ever growing threat.
Before we being, let’s look at a scenario that would best describe a situation that would call for MFA:
You are an IT admin. You are heading to work on what should be a typical Tuesday (or whatever day it may be for you). You sit in traffic, grab your favorite coffee or energy drink, and pull into the parking lot to discover that you must park on the other side of the campus, and walk to the front door, in the pouring rain. To top it off, you forgot your umbrella at home.
You sit at your desk, and open your email client and see that you have an email marked as urgent. It’s from the CFO He/she is frantic, asking you to call them immediately. Just as you are about to call, your CIO calls you and says “YOU NEED TO GET DOWNSTAIRS TO THE BOARD ROOM!” You don’t know what’s going on, but your CIO meets you in the hallway and explains the situation:
Over the weekend, the CFO received an email, saying that there was a parcel waiting for them. There was a link in the email that should have gone to the tracking information. But what it went to was a malicious website. Boom! Malware infected the machine. Passwords were stolen, and now it seems that there were successful attempts to log into the companies SharePoint portal, where sensitive information lay in wait for the remote attacker.
You walk into the board room. The President, CEO, and all shareholders are there. They look at you and the CIO and ask “HOW DID THIS HAPPEN? WHY DON’T WE HAVE ANY METHODS IN PLACE TO CIRCUMVENT THIS????”
Nowadays, this story has become all too common. Whether the attacks are from the outside, or from a disgruntled employee on the inside, securing your data is a must. The days where secure passwords, firewalls, and state of the art anti-malware solutions are gone.
This is scary. How do you stop it? You’ve have everything you could possibly need to prevent this, but there is one exception: a power user. That’s right. No matter how much you educate the end user, it’s hard to keep them abreast of all the nasty security vulnerabilities that are out there. It’s not their fault. It’s not their job to keep up with IT security and possibly threats.
In a world where everyone now has a phone, an email, or some sort of app, there are now ways to use them to your advantage. That my friends, is Multi-Factor Authentication.
Two-factor authentication refers specifically and exclusively to authentication mechanisms where the two authentication elements fall under different categories with respect to “something you have”, “something you are”, and “something you know”.
A multi-step authentication scheme which requires two physical keys, or two passwords, or two forms of biometric identification is not two-factor, but the two steps may be valuable nonetheless. A good example of this is the two-step authentication required by Gmail. After providing the password you’ve memorized, you’re required to also provide the one-time password displayed on your phone. While the phone may appear to be “something you have”, from a security perspective it’s still “something you know”. This is because the key to the authentication isn’t the device itself, but rather information stored on the device which could in theory be copied by an attacker. So, by copying both your memorized password and the OTP (over the phone) configuration, an attacker could successfully impersonate you without stealing anything physical.
The point to multi-factor authentication, and the reason for the strict distinction, is that the attacker must successfully pull off two different types of theft to impersonate you: he must acquire both your knowledge and your physical device, for example. In the case of multi-step (but not multi-factor), the attacker needs only to only pull off one type of theft, just multiple times. So for example he needs to steal two pieces of information, but no physical objects.
Azure Multi-Factor Authentication (MFA) is Microsoft’s two-step verification solution. Azure MFA helps safeguard access to data and applications while meeting user demand for a simple sign-in process. It delivers strong authentication via a range of verification methods, including phone call, text message, or mobile app verification.
Azure Multi-Factor Authentication is an easy to use, scalable, and reliable solution that provides a second method of authentication so your users are always protected.
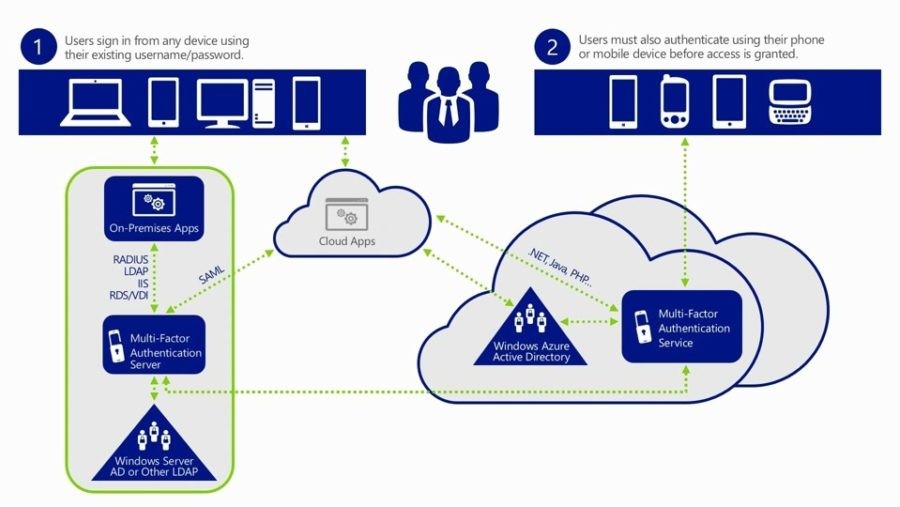
When a user signs in, an additional verification request is sent to the user. The following are a list of methods that can be used for this second verification.
Phone call
A call is placed to a user’s phone asking them to verify that they are signing. Press the # key to complete the verification process. This option is configurable and can be changed to a code that you specify.
Text message
A text message is sent to a user’s smart phone with a 6-digit code. Enter this code in to complete the verification process.
Mobile app notification
A verification request is sent to a user’s smart phone asking them complete the verification by selecting Verify from the mobile app. This occurs if app notification is the primary verification method. If they receive this notification when they are not signing in, they can report it as fraud.
Verification code with mobile app
The mobile app on a user’s device generates a verification code. This occurs if you selected a verification code as your primary verification method.
For the mobile app verification methods, Azure Multi-Factor Authentication works with third-party authentication apps for smart phones. However, we recommend the Microsoft Authenticator app, which is available for Windows PhoneAndroid, and IOS.
There are also advanced configurations that can allow for user self-service functionality.
Great question!
Yes, you are correct. This is an Azure based product. However, the only thing you need is an Azure tenant. That’s right, you heard me. An Azure tenant and MFA subscription. You do not have to sync any users to Azure, nor do you have to create any servers in Azure or any other types of IaaS features. This solution, however, is extendable to Azure if you ever need it in the future.
Beyond the technical functionality that the first two implementations provide, an implementation—hybrid by default—with this product offers:
Azure Multi-Factor Authentication is based on the cloud model. Updates and upgrades are free of charge and communicated beforehand.
Azure MFA is a great multi factor solution. Where you are all for the cloud, or want to keep you important services on-site, Azure MFA can help combat today’s ever increasing password security threat.
Attacks are occurring more often, and weak or stolen user credentials remain the primary entry point for hackers, which is why authentication must be included in your overall security plan. It’s hard enough to keep track of every threat and every new phishing attempt that’s current out in the wild, and it’s even harder ensuring that your users are safe while online as well. Multi-factor authentication is a best-practice approach to help keep user data secure and keep your organization out of the headlines.